An Analysis of the Top 5 Discord Account Takeover Vectors
Blog post description.This article provides a detailed analysis of the five primary vectors for Discord account takeovers: social engineering and phishing, malware-driven token theft, credential stuffing, third-party application exploits, and advanced platform abuse like invite hijacking. Go beyond basic security advice and discover a comprehensive framework for defense, including proactive security measures and a step-by-step incident response plan to protect your digital identity on the platform.
Cliffinkent
7/23/202528 min read


Introduction
Discord has evolved from a niche chat application for gamers into a global communication platform, hosting millions of communities dedicated to interests ranging from education and software development to cryptocurrency trading and art. Its accessibility across desktop, mobile, and web browsers has fueled this massive growth, but it has also made the platform a high-value target for a diverse range of cybercriminals.1 Threat actors now leverage Discord not only to target its vast user base but also as a tool in their own operations, using it for command-and-control (C2) infrastructure, malware hosting, and as a marketplace for illicit tools and stolen data.2
The consequences for a user whose account is compromised are severe and multifaceted. They extend beyond losing access to communities and personal messages to include direct financial loss through unauthorized purchases of premium features like Discord Nitro 3, the use of their trusted identity to propagate malware and phishing scams to friends and server members 4, and the potential for their stolen information to be used in broader identity theft schemes.6 Attackers frequently abuse Discord's own infrastructure, such as its Content Delivery Network (CDN) and Application Programming Interface (API), to distribute malware and exfiltrate stolen data, turning the platform's features against its users.5
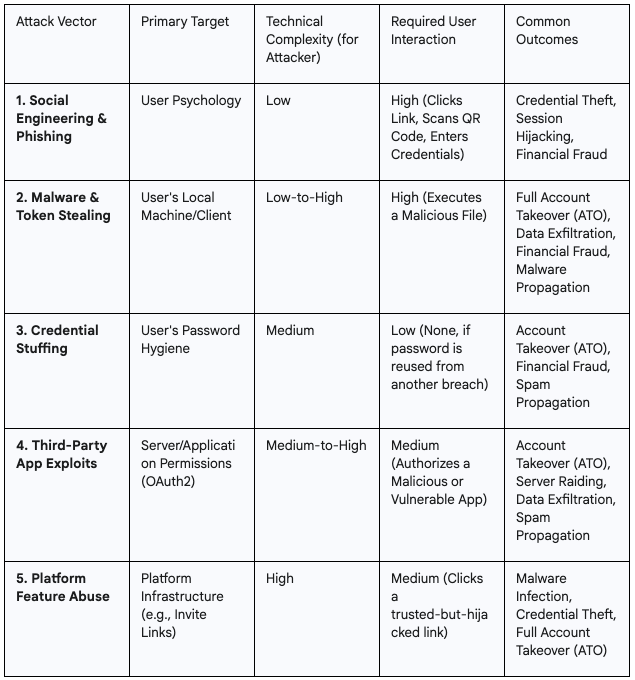
Understanding the methods attackers use is the first step toward building a robust defense. An account compromise on Discord is not a single, monolithic event; it is the result of various attack vectors that differ significantly in technical complexity, required user interaction, and primary target. This report provides an exhaustive analysis of the five primary vectors through which Discord accounts are compromised: Social Engineering and Interactive Phishing, Malware-Driven Credential Exfiltration, Credential Stuffing, Third-Party Application Exploits, and Advanced Platform Feature Abuse. By dissecting the mechanisms, tactics, and underlying security principles of each vector, this analysis aims to equip advanced users, server administrators, and cybersecurity professionals with the nuanced understanding required to effectively secure their presence on the platform.
I. Vector 1: Social Engineering and Interactive Phishing Schemes
The most prevalent and psychologically potent attack vector on Discord targets not a technical flaw in the platform's code, but the user. Social engineering attacks manipulate users into willingly compromising their own accounts by exploiting fundamental human tendencies like trust, greed, and fear. These attacks are effective because they bypass technical defenses by making the legitimate user the instrument of the breach.
The Human as the Endpoint: Principles of Social Engineering on Discord
At its core, social engineering on Discord is the art of deception. Attackers craft narratives and situations designed to lower a user's guard and compel them to perform an action that benefits the attacker. The success of these schemes hinges on the user's gullibility and their response to psychological triggers.8
Two primary tactics underpin most social engineering campaigns on the platform:
Urgency and Fear: Attackers create a false sense of crisis. A user might receive a direct message (DM) claiming their account has been flagged for illicit activity and will be deleted unless they immediately click a link to verify their identity.9 This pressure tactic is designed to induce panic and prevent the user from thinking critically about the request.
Greed and Unrealistic Rewards: The promise of something for free is a powerful lure. Scams offering free access to Discord Nitro, the platform's premium subscription, are exceedingly common and prey on the user's desire for a reward.10
In both cases, the goal is to manipulate the user into either revealing confidential information, such as their login credentials, or performing a sensitive action, like downloading a malicious file or scanning a QR code.12
Anatomy of Common Phishing Lures
Phishing, a subset of social engineering, involves creating fraudulent messages and websites to trick users into handing over sensitive data. On Discord, these lures have evolved into several common forms.
The "Free Nitro" Gambit
The popularity of Discord Nitro makes it the most common bait used in phishing attacks.8 An attacker, often using a bot or a compromised account, will send a user a DM claiming they have won a free Nitro subscription. The message contains a link that directs the user to a phishing website designed to look like a real Discord login page.11 When the user enters their credentials, the attacker captures them. A critical detail for users to check is the domain of the link; any legitimate Nitro gift link will be hosted on the official
discord.gift domain. Any other domain, no matter how similar it looks, is fraudulent.11
Weaponizing Trust: Impersonation
The effectiveness of a phishing attack is dramatically increased when the message comes from a seemingly trustworthy source. Attackers employ several layers of impersonation:
Compromised Friends' Accounts: The most potent phishing messages are those sent from the account of a user's friend.3 Trust is implicit in these relationships, and a user is far more likely to click a link or download a file sent by a known contact, assuming it is legitimate.5 This turns every compromised account into a potential launchpad for further attacks, creating a cascade effect through social networks.
Bots and Influencers: To add a veneer of legitimacy, scammers will create fake bot accounts or impersonate well-known community figures and influencers.7 These accounts may have profile pictures and names that closely mimic the real entity, fooling users who don't look closely.
Discord Staff and Support: A particularly malicious tactic involves impersonating Discord staff members.11 The attacker may claim to be from the "Trust & Safety" team and offer to help with an appeal or a security issue, asking the user for their password or other sensitive information to "verify" their identity.12 Discord has been unequivocal on this point:
official staff will never contact users directly through the Discord application for support-related matters and will never ask for a user's password or authentication token.12
Deceptive Links (Typosquatting)
To make phishing sites appear legitimate, attackers often register domains that are visually similar to Discord's official domains. This technique, known as typosquatting, relies on users not scrutinizing the URL. Examples include using a lowercase "l" instead of an "i" (e.g., dlscord.gift) or using double letters (e.g., diiscrd.com).8 While the presence of
https:// and a lock icon in the browser's address bar can indicate a secure connection, it does not guarantee the site is legitimate, as attackers can also obtain SSL certificates for their phishing domains.9 Vigilant inspection of the full URL is crucial.
The QR Code Login Exploit: Instant Account Takeover
Perhaps the most dangerous interactive phishing attack on Discord is the QR code scam. This method is particularly insidious because it bypasses the need for the user to enter their password and can even circumvent two-factor authentication (2FA).
The attack leverages a legitimate feature. Discord's official QR code login is designed to allow a user to log into the desktop or web client quickly by scanning a code with their already-authenticated mobile app.9 Attackers have weaponized this convenience. The scam follows a predictable pattern:
The attacker sends the victim a DM, typically with a "free Nitro" lure, containing an image of a QR code.
They instruct the victim to scan this code using the scanner in their Discord mobile app to claim the prize.9
The QR code presented to the victim is, in fact, the login QR code from the attacker's own screen.
When the victim scans this code with their authenticated mobile app, they are effectively authorizing the attacker's computer as a new login session for their own account.
The result is an immediate account takeover. The attacker is instantly logged into the victim's account on their own machine, gaining full access without ever needing the password or a 2FA code.9 This represents a significant evolution in phishing tactics. Early schemes focused on stealing static credentials (the password), which could be thwarted by 2FA. The QR code scam, however, targets the dynamic authentication state itself—the live session token. The goal is no longer to steal the user's keys but to trick the user into holding the door open for the attacker.
For users who fall for this scam, there is only one immediate and effective remedy: they must change their account password as quickly as possible. This action invalidates all active authentication tokens and sessions across all devices, which will forcibly log the attacker out of the compromised account.9
II. Vector 2: Malware-Driven Token and Credential Exfiltration
While social engineering preys on user psychology, many of these schemes are merely the delivery mechanism for the ultimate payload: malware. On Discord, the most common and sought-after goal for malware is not just to steal a user's password but to exfiltrate their authentication token. This vector represents a direct assault on the user's machine and the Discord client itself, providing attackers with persistent and unfettered access to an account.
The Primacy of the Authentication Token
To understand this attack vector, one must first understand the role of the authentication token. A Discord token is a long, unique string of characters that the Discord client uses to communicate with Discord's servers after a user has successfully logged in. It essentially functions as a "remember me" key, proving to the server that the user's session is valid.14 For an attacker, this token is the crown jewel.
Value Over Passwords: A stolen token grants immediate and full access to a user's account, completely bypassing the need for a password and, crucially, any enabled two-factor authentication (2FA).15 While a stolen password still requires the attacker to defeat 2FA, a stolen token is a direct key to an authenticated session.17
Complete Impersonation: Once an attacker possesses a user's token, they can make API requests on behalf of the user, allowing them to send messages, join servers, access private chat logs, and change account settings—in short, to do anything the legitimate user can do.18
Invalidation: The single most effective way for a user to invalidate a compromised token is to change their account password. This action forces the generation of a new token and terminates all previous sessions.17 Simply logging out and back in is not a reliable method for regenerating the token.20
Technical Deep Dive: The Mechanics of a Token Stealer
Token-stealing malware is a specific class of information-stealing software (infostealer) designed to locate and exfiltrate these valuable tokens from an infected machine. These programs are highly targeted and operate with precision.
Targeting Local Client Data
The primary method involves scanning the local file system for directories where Discord and modern web browsers store sensitive session data.
Known File Paths: The malware is programmed with a list of default installation paths for various versions of the Discord client (including the stable release, Public Test Build (PTB), and third-party clients like Lightcord) as well as Chromium-based browsers.14 Common target directories include:
%AppData%\Roaming\Discord\Local Storage\leveldb 14
%localappdata%\Discord\app-<version>\modules\discord_desktop_core-1\discord_desktop_core\ 21
Targeted File Types: Within these directories, the stealer searches for specific file types, most notably .ldb files (which are part of the LevelDB database format used by Chromium and Electron apps to store local data) and .log files. The malware then reads the raw contents of these files, using regular expressions to search for strings that match the distinct pattern of a Discord authentication token.14
Client Modification for Persistence
More sophisticated stealers are not content with a one-time data grab. They aim for persistent access by modifying the Discord client application itself. This elevates the threat from a simple compromise to a long-term infection of the user's machine.
A documented technique involves patching a core file of the Discord application named core.asar.21 ASAR is an archive format used by Electron-based applications like Discord to package their source code and resources. By injecting malicious JavaScript code into this file, an attacker can subvert the client's normal functions. For example, the injected code could be programmed to:
Hijack the login event to capture the user's email and password in plaintext as they are typed.
Intercept the new authentication token generated after a password change and immediately exfiltrate it.
Run automatically every time the Discord client is launched, ensuring the attacker always has the most current token.
This method of client modification demonstrates a deeper level of compromise. The client is no longer just a passive container of data to be stolen; it becomes an active, compromised tool working for the attacker. A user who is a victim of this type of attack may find that changing their password is only a temporary solution, as the malware will simply steal the new token upon the next login.
Data Exfiltration
Once the token and other sensitive information (such as saved browser passwords, cookies, and system information) are collected, the malware must send them to the attacker. A common and ironic method is to use Discord's own webhook API. The malware makes a POST request to an attacker-controlled webhook URL, embedding the stolen data in the message. This allows the attacker to receive the stolen credentials as a new message in their own private Discord server, effectively using Discord's infrastructure to facilitate the attack.22
The Infostealer Ecosystem and Distribution
Discord token theft is not the work of a few isolated hackers. It is part of a mature and widespread criminal ecosystem.
Prominent Malware Families: Many of the most prevalent infostealers and Remote Access Trojans (RATs) in the wild today include built-in modules specifically designed to steal Discord tokens. Well-known examples include AsyncRAT 24,
Lumma Stealer 25,
Katz Stealer 26,
Arcane Stealer 27, and malware specifically classified as
Spyware.DiscordStealer.18 Many of these are sold on a Malware-as-a-Service (MaaS) basis, where aspiring criminals can pay a subscription fee for access to the malware, a control panel, and updates.25Common Distribution Channels: This malware reaches victims through several channels, often originating from social engineering:
Trojanized Software: The most common delivery method is disguising the malware as a desirable program, such as a video game cheat, a software "crack," or a utility tool. These are often promoted in YouTube video descriptions or shared directly within Discord servers.27
Malicious Files on Discord CDN: Attackers frequently upload their malware directly to a Discord channel. This generates a cdn.discordapp.com link, which they can then share. To many users, a link from Discord's own CDN appears more trustworthy than one from an unknown file-sharing site, increasing the likelihood they will download and run the file.2
Corrupted Installers: Attackers create and distribute fake installers for the Discord client itself. Users who download the application from an unofficial source may unknowingly be installing a version bundled with malware.5
The existence of malware "generators" 23 and MaaS platforms has democratized this form of cybercrime. It means that non-technical actors can easily acquire and deploy sophisticated, obfuscated malware with pre-built Discord token stealing capabilities. This dramatically increases the volume of attacks and explains why so many users are targeted with similar malware payloads. The defensive challenge is no longer about tracking a few skilled threat groups but about protecting against a commoditized, widely distributed set of criminal tools.
III. Vector 3: Large-Scale Automated Credential Stuffing Attacks
Distinct from targeted phishing or malware infections, credential stuffing is an impersonal, brute-force method of account takeover that operates on a massive scale. This vector does not rely on tricking a specific user or infecting their machine. Instead, it exploits a systemic weakness in online security: the widespread human habit of reusing passwords across multiple services.
Exploiting Systemic Password Reuse
The fundamental principle of a credential stuffing attack is simple yet devastatingly effective. Attackers obtain large lists, often containing millions or even billions, of username and password combinations that have been exposed in data breaches from other websites and services.29 They then use automated software to systematically "stuff" these credentials into the login forms of other, unrelated services like Discord, betting that a percentage of users have reused the same email and password combination.30
The Power of Scale: While the success rate for any single login attempt is extremely low—often estimated around 0.1%—the sheer volume of credentials tested makes the attack worthwhile for criminals.30 A list of one million breached credentials could yield around 1,000 successful account takeovers on Discord.
Password Complexity is Not a Defense: A key distinction between credential stuffing and traditional brute-force attacks is that the latter involves guessing passwords from scratch. Credential stuffing, by contrast, uses credentials that are already known to be valid for the user on at least one other service.30 This means that even a long, complex password offers no protection if it has been reused and exposed in a previous data breach.
The Root Vulnerability: The attack's success is predicated entirely on user behavior. Studies have suggested that a significant majority of internet users, by some estimates as high as 85%, reuse passwords across multiple sites.30 This single behavioral flaw creates a persistent and widespread vulnerability that affects nearly every online platform with a login form.
This dynamic means that the security of a user's Discord account is inextricably linked to the security of every other online service they use. A data breach at a small e-commerce site or an old forum can directly lead to the compromise of a user's Discord account if they shared the same password.
Anatomy of a Credential Stuffing Campaign
These attacks are not manual; they are highly automated, coordinated campaigns designed to maximize efficiency and evade detection.
Sourcing Credentials: The process begins with credential acquisition. Attackers obtain massive "combo lists" (formatted as email:password) from various sources, including public data breach compilations like "Collection #1," logs from widespread info-stealer malware campaigns, and underground cybercrime marketplaces where breach data is traded and sold.29
Automation and Tooling: Attackers employ specialized software, such as the popular tool OpenBullet, to automate login attempts at an industrial scale.29 These tools are configured to send thousands of login requests per minute, testing each credential pair from the combo list against Discord's login endpoint.
Evasion Techniques: Discord and other platforms have defenses to detect and block such automated attacks, such as rate limiting (blocking an IP address after too many failed logins). To circumvent these protections, attackers use sophisticated evasion techniques:
Proxy Rotation: The attack traffic is routed through vast networks of proxy servers or botnets. This makes the login attempts appear to originate from thousands of different legitimate IP addresses around the world, making it difficult to block the attack based on its source.29
Behavioral Mimicry: The automation tools are configured to make the malicious traffic look as human as possible. They can randomize HTTP headers and user-agent strings to avoid simple device fingerprinting, and they can throttle the speed of login attempts to mimic human pacing.29 The goal is to make the attacker's login attempts indistinguishable from the normal flow of login traffic.30
Monetization of "Hits": When a login attempt is successful, the valid credential pair is logged as a "hit." These compromised accounts are then immediately monetized. An attacker might use a linked credit card to purchase and gift Discord Nitro, use the account's trusted identity to spread phishing links to the user's friends, or sell the validated account credentials on dark web forums.3
The extensive use of these evasion tactics reveals a key strategic objective of the attacker: to blend in with legitimate traffic. This creates a difficult security challenge for platforms, which must tune their defenses to block malicious bots without inadvertently locking out legitimate users. This has led to a security "arms race," with attackers constantly refining their automation to better mimic human behavior, and defenders deploying increasingly advanced behavioral analysis and machine learning models to detect the subtle anomalies that betray the presence of a bot.32
Defense Against Credential Stuffing
Given that the attack exploits user behavior, the defenses must address both the user and the platform.
User-Side Defenses: The responsibility on the user is clear and critical.
Unique Passwords: The single most effective defense is to use a strong, unique password for Discord that is not used on any other website or service. Using a password manager is the most practical way to achieve this across all online accounts.4
Two-Factor Authentication (2FA): Enabling 2FA provides a crucial second layer of security. Even if an attacker obtains a user's correct password through a credential stuffing attack, they will be unable to log in without the time-sensitive code from the user's authenticator app.9
Platform-Side Defenses: Discord and other services deploy a range of technologies to combat these automated attacks, including rate limiting, IP-based blocking, CAPTCHA challenges to distinguish humans from bots, and advanced anomaly detection systems that can identify suspicious login patterns (e.g., a high volume of failed logins from a single location or a single account being accessed from multiple geographically disparate locations in a short time).31
IV. Vector 4: Exploitation of the Third-Party Application Ecosystem
Discord's power and appeal are significantly enhanced by its rich, open ecosystem of third-party applications, primarily bots and services that integrate via the OAuth2 protocol. While this ecosystem fosters innovation and allows for deep customization of communities, it also introduces a substantial and complex attack surface. Compromises in this vector occur not by attacking the user's credentials directly, but by exploiting the trust and permissions granted to these external applications.
Bot-Centric Threats: Trojan Horses in Your Server
Bots are integral to the functionality of most large Discord servers, handling everything from moderation and user verification to music playback and games. However, this integration creates a relationship of trust that can be exploited in several ways.
The Danger of Over-Privileged Bots
A common but critical mistake made by server administrators is granting bots excessive permissions for the sake of convenience. Many administrators will assign a new bot the "Administrator" role, which gives it every permission on the server, including the ability to manage channels, roles, and members.39 This violates the fundamental security principle of least privilege.
If a bot with administrator privileges is compromised—either through a vulnerability in its own code or because the developer's account was hacked—the consequences for the server can be catastrophic. The attacker, controlling the bot, could instantly ban all members, delete all channels and roles, send malicious links to everyone in the server, or silently exfiltrate private data.39 For this reason, bots should only ever be granted the specific, granular permissions they require to perform their intended functions.39
Malicious and Vulnerable Bots
The decentralized nature of the bot ecosystem means there is no central body for quality assurance or security vetting. Anyone can code and host a Discord bot. This leads to two primary risks:
Intentionally Malicious Bots: Attackers create bots that are explicitly designed to be malicious from the outset. These may be advertised as having useful features, but once added to a server and granted permissions, they execute their true purpose, such as spamming users or raiding the server.39 Some malicious bots are designed to trick users into authorizing them via OAuth2, and then abuse the "Join Servers for You" permission to force the user's account to join hundreds of spam servers.41
Vulnerabilities in Legitimate Bots: Even well-intentioned bots created by legitimate developers can contain programming flaws that create security vulnerabilities. These are often unintentional but can be just as dangerous. Common vulnerabilities found in third-party Discord bots include:
Remote Code Execution (RCE): A flaw in how a bot processes user-provided input can allow an attacker to execute arbitrary code on the server where the bot is hosted. A documented case involved the popular Red-DiscordBot, where a specially crafted "going live" status message could be used to inject and execute Python code.42 Another RCE was found in the Discord-Recon bot due to improper input sanitization.43
Information Disclosure: A vulnerability in the MIT IdentiBot, which was designed to verify users' affiliation with the university, allowed any user to join the bot to their own server and use its commands to query for the private information (full name, etc.) of any other user who had previously verified with the bot.44
The security of a Discord server is, therefore, only as strong as the most insecure bot it has installed. Each bot added is an extension of the server's trust boundary, and a vulnerability in any one of them can compromise the entire community.
OAuth2 Application Vulnerabilities: The Perils of "Log in with Discord"
The OAuth2 framework allows users to grant third-party applications limited access to their Discord account without sharing their password. This is the mechanism behind "Log in with Discord" buttons and services that can, for example, view a user's connected accounts or join servers on their behalf. While convenient, this creates another avenue for account compromise.
Risks for Users: Authorizing Malicious Applications
When a user clicks to authorize an application, Discord presents them with a consent screen detailing exactly what permissions (known as "scopes") the application is requesting.45 If a user approves a malicious application, they are effectively handing the attacker a long-lived access token that can be used to abuse those permissions.41 It is critical for users to carefully review the scopes an application requests before clicking "Authorize." If an app that claims to only show statistics is asking for permission to send messages as you, that is a major red flag. Users should regularly audit the applications they have connected to their account in
User Settings > Authorized Apps and deauthorize any they no longer use or recognize.12
Risks for Developers (and their Users)
A more sophisticated attack on this vector targets not the end-user, but the developer of the third-party application. Even a security-conscious user can be compromised if they use a legitimate application that has been coded insecurely by its developer.
Leaked Client Credentials: To interact with Discord's API, a developer's application has a unique client_id and a client_secret. These should be treated with the same care as a password. A common developer mistake is to hardcode these secrets directly into their application's source code, which may then be uploaded to a public GitHub repository.46 Attackers constantly scan public repositories for these leaked credentials. If found, they can use them to impersonate the legitimate application, potentially leading to large-scale phishing attacks against its users.
Redirect URI Manipulation: This is a classic and critical OAuth2 vulnerability. After a user authorizes an application, Discord redirects them back to the application using a pre-registered redirect_uri, sending a temporary authorization code in the URL. The application then exchanges this code for a permanent access token. If the application does not strictly validate that the redirect_uri in the request matches its pre-registered URI, an attacker can manipulate the flow. They can trick the user into starting the authorization process with a malicious redirect_uri, causing Discord to send the user's authorization code to an attacker-controlled server instead of the legitimate application.47 The attacker can then use this code to get an access token and take over the user's account within the scope of that application.
This highlights how OAuth2 exploits shift the focus of the attack from the end-user's security practices to the code quality and security posture of the entire developer ecosystem that integrates with Discord.
V. Vector 5: Advanced Platform Exploitation via Invite Link Hijacking
Beyond attacks that target users or third-party code, a more advanced class of exploit targets the inherent logic and features of the Discord platform itself. The most prominent example of this is invite link hijacking, a sophisticated vector that weaponizes a core community-building feature—server invites—to create a highly effective and deceptive attack funnel. This method was analyzed in detail in research by Check Point, which uncovered an active campaign using this technique to deliver malware.50
Weaponizing a Platform Feature: The Mechanics of Invite Hijacking
The vulnerability does not lie in a traditional software bug but in the lifecycle management of Discord's invite links, particularly custom or "vanity" URLs (e.g., discord.gg/yourbrand).
The Vanity URL Lifecycle: To obtain a custom vanity URL, a server must achieve a certain "Boost" level, which is a premium status often maintained through paid subscriptions. If the server loses its Boost status (for example, due to a missed payment), the vanity URL is invalidated and released back into a general pool of available names.50
Hijacking the Link: Threat actors actively monitor for desirable, previously trusted vanity URLs to become available. These are often URLs that have been widely publicized by brands, games, or large communities on their official websites, social media profiles, and forums. As soon as a trusted URL is released, the attacker claims it for their own malicious server, which must also have the required Boost level.50
Exploiting Temporary Links: A similar principle can apply to some regular, randomly-generated invite links. After a temporary invite code expires, it is sometimes possible for an attacker to register that same code string as a new vanity URL for their malicious server.50
This attack vector represents the erosion of what should be a stable "digital trust anchor." A user may see a link like discord.gg/OfficialGame on the game's official website and correctly assume it is safe. However, if that link has been hijacked, clicking on it will lead them not to the official server, but to the attacker's trap. The trust associated with the URL becomes decoupled from its destination, making it a powerful tool for deception.
The Attack Chain: From Trusted Link to Malware Infection
The hijacked link is the entry point to a carefully orchestrated, multi-stage attack designed to compromise the user's machine.
Redirection from a Trusted Source: The attack begins when a user clicks a link they believe to be legitimate. Because the invite URL has been hijacked, they are seamlessly redirected to the attacker's server without any warning.50
The Fake "Verification" Funnel: The attacker's server is designed to mimic the appearance of the original, legitimate server. However, all channels are locked except for a single channel, typically named #verify or #welcome. This funnels the new user into a controlled environment.50
The Malicious Bot and Phishing Site: Inside the verification channel, a fake bot (e.g., one named "Safeguard") instructs the user that they must complete a verification step to gain access to the rest of the server. Clicking the "Verify" button initiates an OAuth2 authentication flow that redirects the user to a phishing website meticulously designed to look like an official Discord page.50
Multi-Stage Malware Delivery: The phishing site employs a social engineering technique known as "ClickFix." It preloads a malicious PowerShell command onto the user's clipboard and provides on-screen instructions that trick the user into opening the Windows Run dialog (Win+R), pasting the command, and executing it.50 This initial script acts as a "loader" and begins a multi-stage infection process. To evade detection by antivirus software and automated sandbox analysis, the loader downloads subsequent payloads from legitimate, trusted services like GitHub, Bitbucket, and Pastebin. This "low-and-slow" approach, which often includes time-based delays between stages, helps the malware fly under the radar of security tools that look for rapid, overtly malicious behavior.50 The final payload is typically a powerful Remote Access Trojan (RAT) like AsyncRAT or a credential-stealing malware like the Skuld Stealer, which targets cryptocurrency wallets.50
The real-world campaign investigated by Check Point Research demonstrated the global reach and effectiveness of this vector, with victims identified across the United States, Europe, and Asia.51 The sophistication of this attack lies not in heavy code obfuscation, but in its clever combination of a platform exploit (invite hijacking), social engineering, and the abuse of legitimate internet services to hide its malicious traffic in plain sight.
The most effective defense for server owners against this specific vector is to use permanent, non-vanity invite links for public promotion, as these are significantly more resistant to being hijacked.50
VI. A Framework for Comprehensive Defense and Incident Response
Securing a Discord account against a diverse and evolving threat landscape requires a multi-layered, defense-in-depth strategy. It is not enough to guard against a single vector; users must adopt a holistic security posture that addresses psychological manipulation, technical vulnerabilities, and ecosystem risks. This framework consolidates the preceding analysis into a set of proactive defenses and a clear, actionable incident response plan for advanced users.
Proactive Defense-in-Depth: An Expert's Security Checklist
This checklist outlines the essential, non-negotiable practices for hardening a Discord account and minimizing its attack surface.
Account Hygiene:
Password Security: Use a long, complex, and, most importantly, unique password for your Discord account. This is the single most effective defense against credential stuffing. Employ a trusted password manager to generate and store unique passwords for all online services.4
Two-Factor Authentication (2FA): Enable 2FA using an authenticator app (e.g., Google Authenticator, Authy).13 Avoid using SMS-based 2FA if possible, as it is vulnerable to SIM-swapping attacks.6 Securely store your 2FA backup codes in a safe, offline location, such as a physical document or an encrypted file.4
Interaction Prudence:
Scrutinize All Unsolicited Contact: Be deeply skeptical of any unexpected DMs, especially those offering free items (like Nitro), creating a sense of urgency, or asking for personal information.9
Link and File Safety: Never click on links or download files from unknown or untrusted sources. This applies even to links from friends, as their accounts may be compromised. Use a URL scanning service like VirusTotal to check suspicious links before clicking.19
The QR Code Rule: Adopt a zero-trust policy for QR codes. Never scan a QR code sent to you by another user in Discord. The feature is only for logging yourself into Discord's desktop or web clients from the official site.9
Privacy Settings Configuration:
Control Incoming DMs: In User Settings > Privacy & Safety, disable the "Allow direct messages from server members" setting on a per-server basis for any large, public communities you join. This significantly reduces your exposure to unsolicited phishing and spam messages.13
Utilize Filters: Ensure the "DM Spam Filter" is enabled to automatically filter messages from non-friends that may contain spam. Configure the "Sensitive Media Filters" according to your preference.13
Third-Party Application Security:
Audit Authorized Apps: On a regular basis, navigate to User Settings > Authorized Apps and review the list of applications and bots that have access to your account. Deauthorize any service you no longer use or do not recognize.12
Vet New Bots: When adding a bot to a server you manage, only use bots from reputable, well-known sources. Carefully review the permissions the bot requests during the authorization process and deny overly broad permissions like "Administrator" whenever possible.39
Local Device Security:
Anti-Malware Software: Use a reputable, up-to-date antivirus or anti-malware solution on your computer. This is your primary defense against token stealers and other infostealing malware.3
Physical Security: Never leave your computer unlocked and unattended. When using a public or shared computer to access Discord, always use the browser's incognito or private mode to ensure your login information is not saved.4
Early Warning: Recognizing the Indicators of Compromise (IoCs)
Recognizing the signs of a hack early is critical to mitigating the damage. Be vigilant for the following indicators:
Unusual Account Activity: You notice messages, friend requests, or server invites being sent from your account that you did not initiate. Your account suddenly joins new servers you don't recognize. Your profile picture, username, or other settings are changed without your knowledge.3
Suspicious Notifications: You receive official emails from Discord notifying you of a login from a new IP address or a password reset attempt that you did not perform.3
Unexpected 2FA Prompts: You receive a notification from your authenticator app with a 2FA code for Discord when you are not actively trying to log in. This is a critical warning sign that an attacker has your password and is attempting to bypass your 2FA.3
Unexplained Financial Transactions: You see charges on your linked credit card or bank account for Discord Nitro purchases or gifts that you did not make.3
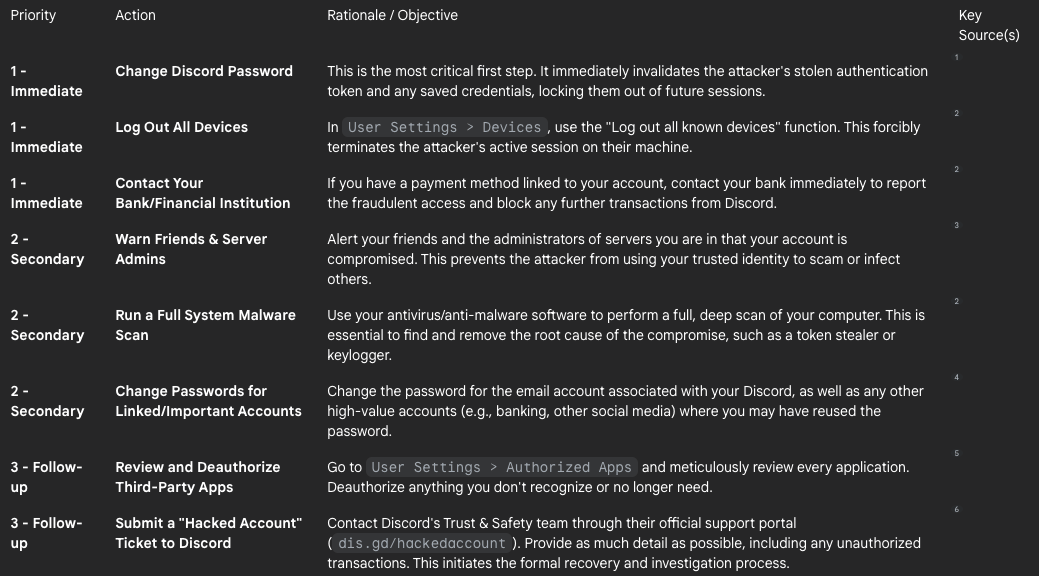
Incident Response Playbook: A Step-by-Step Guide
If you suspect your account has been compromised, it is crucial to act quickly and methodically. Panic can lead to mistakes; follow this prioritized checklist to contain the threat and begin the recovery process.
Conclusion
The security of a Discord account is not a simple matter of having a strong password. It is a complex, multifaceted challenge that requires a sophisticated, defense-in-depth strategy. The analysis of the five primary account takeover vectors reveals a threat landscape where attackers target every layer of the system: the user's psychology through social engineering; the user's local machine through malware and token stealers; the user's security habits through credential stuffing; the third-party developer ecosystem through bot and OAuth2 exploits; and the platform's own features through advanced invite hijacking.
A clear pattern emerges from this analysis: threat actors are adaptive and opportunistic. When one defense, like 2FA, becomes widespread, they evolve their tactics to circumvent it, as seen with the rise of token-stealing malware and QR code scams. They leverage the platform's greatest strengths—its open API, vast user base, and customizable nature—and turn them into weapons. The decentralization of the bot ecosystem fosters innovation but creates a distributed and difficult-to-manage attack surface. The trust inherent in social networks is systematically exploited to propagate attacks from one compromised account to the next.
Ultimately, securing a presence on Discord is a shared responsibility. The platform must continue to enhance its built-in security features, such as proactive spam filtering, bot detection, and secure defaults. The developer community must adhere to secure coding practices, particularly around the handling of API secrets and OAuth2 implementations, to protect their users. However, the final and most critical line of defense is the user.
For the expert user, security is not a one-time setup but a continuous process of vigilance, education, and adaptation. It requires maintaining impeccable account and device hygiene, exercising a zero-trust mindset when interacting with unsolicited messages and applications, and understanding the subtle indicators of compromise. As Discord continues to grow and integrate more deeply with financial systems, creator economies, and other platforms, its value as a target will only increase. The attack vectors will become more novel and sophisticated, demanding an ever-more-nuanced understanding from those who wish to navigate its vibrant but perilous digital spaces securely.
Works cited
Is Discord Safe to Use in 2024? Essential Tips to Use Discord Safely - Mysterium VPN, accessed on July 23, 2025, https://www.mysteriumvpn.com/blog/is-discord-safe
Cyber Research on the Malicious Use of Discord - CYFIRMA, accessed on July 23, 2025, https://www.cyfirma.com/research/cyber-research-on-the-malicious-use-of-discord/
What to do if your Discord account is hacked - NordVPN, accessed on July 23, 2025, https://nordvpn.com/blog/discord-account-hacked/
Discord Best Practices: Guidelines on how to keep Discord safe and secure - DotCIO, accessed on July 23, 2025, https://itssc.rpi.edu/hc/en-us/articles/32018134944013-Discord-Best-Practices-Guidelines-on-how-to-keep-Discord-safe-and-secure
What Is Discord Malware? - Check Point Software, accessed on July 23, 2025, https://www.checkpoint.com/cyber-hub/threat-prevention/what-is-malware/what-is-discord-malware/
Discord Data Breach: What Happened And How To Protect Your Account - Onerep, accessed on July 23, 2025, https://onerep.com/blog/discord-data-breach-how-to-protect-your-account
Discord: The New Playground for Cybercriminals - SOCRadar® Cyber Intelligence Inc., accessed on July 23, 2025, https://socradar.io/discord-the-new-playground-for-cybercriminals/
How easy is it to get hacked in Discord? - Quora, accessed on July 23, 2025, https://www.quora.com/How-easy-is-it-to-get-hacked-in-Discord
Securing Your Discord Account, accessed on July 23, 2025, https://discord.com/safety/securing-your-discord-account
Discord Scam Fraud - Action Fraud Claims Advice, accessed on July 23, 2025, https://www.actionfraud.org.uk/discord-scam-fraud/
These 11 New Discord Scams Can (and Will) Steal Your Data - Aura, accessed on July 23, 2025, https://www.aura.com/learn/discord-scams
My Discord Account was Hacked or Compromised, accessed on July 23, 2025, https://support.discord.com/hc/en-us/articles/24160905919511-My-Discord-Account-was-Hacked-or-Compromised
Four Steps to a Safer Account | Discord Safety, accessed on July 23, 2025, https://discord.com/safety/360043857751-four-steps-to-a-super-safe-account
Malicious npm Packages Are After Your Discord Tokens - JFrog, accessed on July 23, 2025, https://jfrog.com/blog/malicious-npm-packages-are-after-your-discord-tokens-17-new-packages-disclosed/
Security measures against token stealers/AnarchyGrabber - Discord Support, accessed on July 23, 2025, https://support.discord.com/hc/en-us/community/posts/4412312139031-Security-measures-against-token-stealers-AnarchyGrabber
Token Stealing Prevention - Discord Support, accessed on July 23, 2025, https://support.discord.com/hc/en-us/community/posts/7333003562775-Token-Stealing-Prevention
A compromised account - Discord Support, accessed on July 23, 2025, https://support.discord.com/hc/en-us/community/posts/21922044087959-A-compromised-account
Spyware.DiscordStealer - Malwarebytes, accessed on July 23, 2025, https://www.malwarebytes.com/blog/detections/spyware-discordstealer
Safety Library | Discord, accessed on July 23, 2025, https://discord.com/safety-library
Discord Tokens, accessed on July 23, 2025, https://support.discord.com/hc/en-us/community/posts/360049324394-Discord-Tokens
Info Stealer Abusing Codespaces Puts Discord Users at Risk | Trend Micro (US), accessed on July 23, 2025, https://www.trendmicro.com/en_us/research/23/e/info-stealer-abusing-codespaces-puts-discord-users--data-at-risk.html
Info-Stealer Malware Disguised as Illegal Pornography Being Distributed via Discord, accessed on July 23, 2025, https://asec.ahnlab.com/en/24512/
Here Comes TroubleGrabber: Stealing Credentials Through Discord - Netskope, accessed on July 23, 2025, https://www.netskope.com/blog/here-comes-troublegrabber-stealing-credentials-through-discord
Unmasking AsyncRAT: Navigating the labyrinth of forks - WeLiveSecurity, accessed on July 23, 2025, https://www.welivesecurity.com/en/eset-research/unmasking-asyncrat-navigating-labyrinth-forks/
June 2025 Malware Spotlight: Discord Exploits Lead to Rising Threats - Check Point Blog, accessed on July 23, 2025, https://blog.checkpoint.com/research/june-2025-malware-spotlight-discord-exploits-lead-to-rising-threats/
Katz Stealer | Powerful MaaS On the Prowl for Credentials and Crypto Assets - SentinelOne, accessed on July 23, 2025, https://www.sentinelone.com/blog/katz-stealer-powerful-maas-on-the-prowl-for-credentials-and-crypto-assets/
New Arcane stealer spreading via YouTube and Discord - Securelist, accessed on July 23, 2025, https://securelist.com/arcane-stealer/115919/
My laptop got infected with token logger, infostealer how to remove it? - Learn Microsoft, accessed on July 23, 2025, https://learn.microsoft.com/en-us/answers/questions/3847179/my-laptop-got-infected-with-token-logger-infosteal?forum=windows-all&referrer=answers
Credential stuffing attacks: anatomy, detection, and defense - The Castle blog, accessed on July 23, 2025, https://blog.castle.io/credential-stuffing-attacks-anatomy-detection-and-defense/
Credential stuffing vs. brute force attacks | Cloudflare, accessed on July 23, 2025, https://www.cloudflare.com/learning/bots/what-is-credential-stuffing/
What is Credential Stuffing? | Credential Stuffing Attack - Azion, accessed on July 23, 2025, https://www.azion.com/en/learning/bots/what-is-credential-stuffing/
How to Stop Credential Stuffing Attacks? | Indusface Blog, accessed on July 23, 2025, https://www.indusface.com/blog/credential-stuffing-prevention-how-to-stop-and-mitigate-credential-stuffing-attacks/
Credential Stuffing Attacks | Group-IB Knowledge Hub, accessed on July 23, 2025, https://www.group-ib.com/resources/knowledge-hub/credential-stuffing-attacks/
No, the 16 billion credentials leak is not a new data breach - Bleeping Computer, accessed on July 23, 2025, https://www.bleepingcomputer.com/news/security/no-the-16-billion-credentials-leak-is-not-a-new-data-breach/
How to Prevent Credential Stuffing [9 Best Practices] - StrongDM, accessed on July 23, 2025, https://www.strongdm.com/blog/credential-stuffing-prevention
How to Prevent Credential Stuffing Attacks: 5 Strategies for 2024 - DataDome, accessed on July 23, 2025, https://datadome.co/guides/credential/how-to-prevent-credential-stuffing-strategies/
Credential Stuffing: What It Is and How to Prevent It? - Authgear, accessed on July 23, 2025, https://www.authgear.com/post/credential-stuffing
Credential Stuffing Prevention - OWASP Cheat Sheet Series, accessed on July 23, 2025, https://cheatsheetseries.owasp.org/cheatsheets/Credential_Stuffing_Prevention_Cheat_Sheet.html
The 10 Most Common Discord Security Risks and How to Avoid Them - Keywords Studios, accessed on July 23, 2025, https://www.keywordsstudios.com/en/about-us/news-events/news/the-10-most-common-discord-security-risks-and-how-to-avoid-them/
Discord - Permissions by Categories, Channels and Roles Explained - Mava, accessed on July 23, 2025, https://www.mava.app/blog/discord-permissions-by-categories-channels-and-roles-explained
This is getting serious - Discord Support, accessed on July 23, 2025, https://support.discord.com/hc/en-us/community/posts/360051613173-This-is-getting-serious
CVE-2020-15147: Remote Code Execution in Red Discord Bot | CVE Database - Miggo, accessed on July 23, 2025, https://www.miggo.io/vulnerability-database/cve/CVE-2020-15147
Vulnerability Details : CVE-2024-21663 - Discord-recon, accessed on July 23, 2025, https://www.cvedetails.com/cve/CVE-2024-21663/
CVE-2024-35237 - Red Hat Customer Portal, accessed on July 23, 2025, https://access.redhat.com/security/cve/cve-2024-35237
Discord oAuth2 Question · pocketbase pocketbase · Discussion #2672 - GitHub, accessed on July 23, 2025, https://github.com/pocketbase/pocketbase/discussions/2672
Remediating Discord Oauth2 Key leaks | GitGuardian, accessed on July 23, 2025, https://www.gitguardian.com/remediation/discord-oauth2-key
Common Security Issues in Implementing OAuth 2.0 and How to Mitigate Them, accessed on July 23, 2025, https://www.pullrequest.com/blog/common-security-issues-in-implementing-oauth-2-0-and-how-to-mitigate-them/
Common OAuth Vulnerabilities - Doyensec's Blog, accessed on July 23, 2025, https://blog.doyensec.com/2025/01/30/oauth-common-vulnerabilities.html
OAuth 2.0 authentication vulnerabilities | Web Security Academy - PortSwigger, accessed on July 23, 2025, https://portswigger.net/web-security/oauth
From Trust to Threat: Hijacked Discord Invites Used for Multi-Stage Malware Delivery, accessed on July 23, 2025, https://research.checkpoint.com/2025/from-trust-to-threat-hijacked-discord-invites-used-for-multi-stage-malware-delivery/
Hijacked Trust: How Malicious Actors Exploited Discord's Invite ..., accessed on July 23, 2025, https://blog.checkpoint.com/research/hijacked-trust-how-malicious-actors-exploited-discords-invite-system-to-launch-global-multi-stage-attacks/
Tips: Keeping Account As Safe As Possible! : r/discordapp - Reddit, accessed on July 23, 2025, https://www.reddit.com/r/discordapp/comments/qohsva/tips_keeping_account_as_safe_as_possible/
8 Steps to Protect Your Account and Data When Using Discord - Bitdefender, accessed on July 23, 2025, https://www.bitdefender.com/en-gb/blog/hotforsecurity/8-steps-to-protect-your-account-and-data-when-using-discord
Discord Account Hacked: Here's What To Do Now | All About Cookies - AllAboutCookies.org, accessed on July 23, 2025, https://allaboutcookies.org/discord-account-hacked
How to tell if someone has hacked into your discoed account : r/discordapp - Reddit, accessed on July 23, 2025, https://www.reddit.com/r/discordapp/comments/cblgd8/how_to_tell_if_someone_has_hacked_into_your/
What If My Discord Account Got Hacked | AdsPower, accessed on July 23, 2025, https://www.adspower.com/blog/what-if-my-discord-account-got-hacked